My First College Offline Hackathon
I and my friends recently participated in a College level IdeathonX'2023 Mega IT Hackathon where
we were given a problem statement from the Kavach'2023 Hackathon.
Problem Statement
New age women’s safety app
Description
Design and develop a Women’s safety app that automatically senses the danger to a mobile user and triggers an SOS alert with location details based on multimodal data from a mobile device such as audio, video, image, motion detection, etc., given a situation that the user is not able to operate the mobile.
Tech Stacks
Flutter for Front-end, Firebase for Back-end, Python libraries like OpenCV for Image Recognition
My Experience
It was a great learning experience for me as well as for my team, we were involved in a Hybrid 36-hours
hackathon, and we used to skip our college classes for discussing the ideas. The most challenging part was the night before the hackathon Grand Finale where our team witnessed several blockades like in the front end part which was under my belt I received several bugs related to Google Authentication, Firebase, and Flutter integration.
The voice recognition module that was under my colleague, faced errors that seems impossible to solve at
that moment. But after spending the whole night debugging and fixing errors we finally made it work. The front end was
ready and everything worked except one important part that we were still missing.
That part was the integration of Python modules with Flutter, our team realized a lot later that the integration of Python and Flutter for running ML libraries will require a completely different set of libraries, these libraries come under Android ML kit and Tensorflow Lite or tflite. It was quite a low time for all of us but without wasting any time we started figuring out how to write Python code in Flutter. Hehe, ChatGPT did help us with this task
but still, the errors didn’t leave us and we were bombarded with loads of them. But as programmers, we know
errors are an integral part of our daily lives, we began researching about them and came up with different ways to fix them but ended up solving only a few not all.
The Day Of Final Judgement
Finally, our team reached the offline hackathon arena where we were allowed to work on our project for the next 3 hours before the final evaluation. The evaluation takes place in three rounds, all three rounds welcomed new guests and evaluators from AICTE and other colleges. Our team leader greeted all of them with warmth and there goes our first pitch which included the explanation of our Team name which was $WhoAmI
Why $WhoAmI ?
$WhoAmI is a famous Linux command which shows the currently logged-in user. We came up with the name because we all believe in Linux philosophy which is to know what you are doing, Linux is open source and provides us security that no other operating system at present does. We chose this name since our Kavach problem statement requires us to build an app for women’s safety so that women can freely represent themselves in our society.
The freedom that Linux gives us somewhat resonates with the idea of our app which aims at providing freedom
to women.
Ok continuing with the pitch, the judges asked us about our tech stacks, why we chose these technologies for this task, and how it is better than any other technology. I would like to thank our team leader for managing everything so well and for creating such a remarkable presentation.
Our Logo

App UI
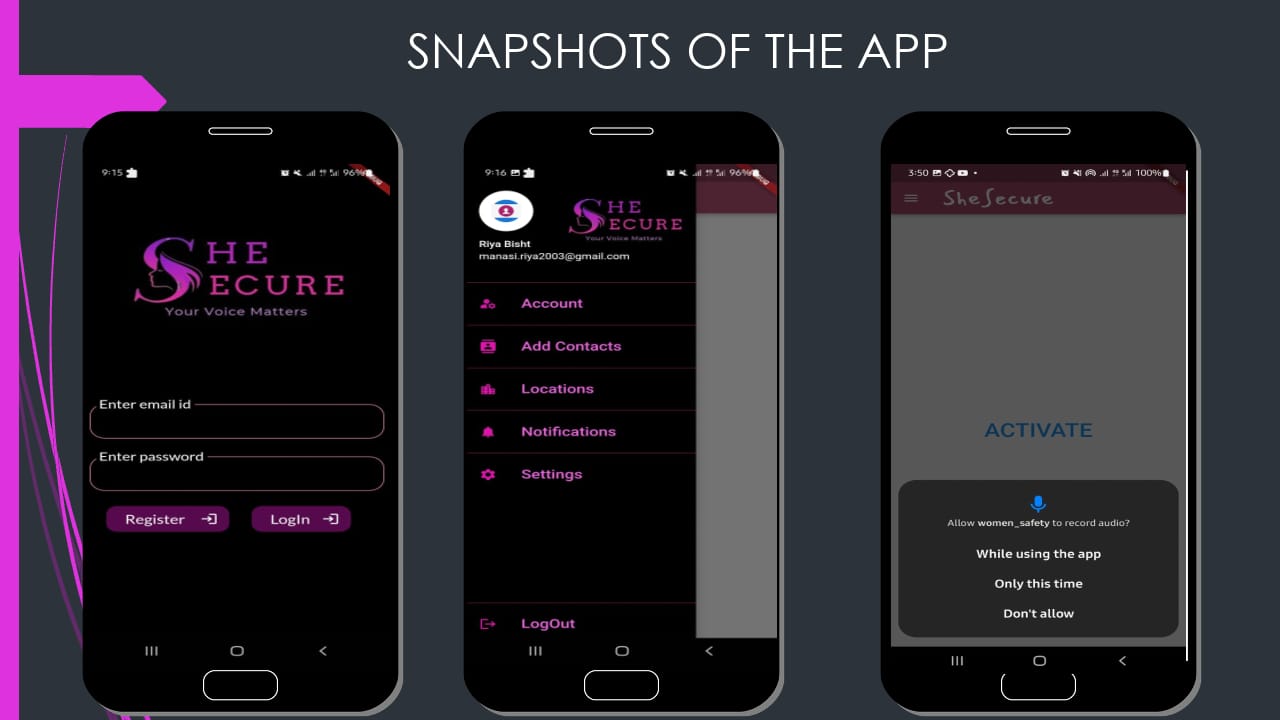
Future Plans
Since the problem statement is a real-life issue that our society must need, we would
like to continue working on this project and will see if we can one day upload our app to the PlayStore.
Currently, the plan would be to make this project open source so that it can be improved and new contributors can gain from it.
Conclusion
It did seem impossible at the start but with great team efforts and proper management, everything can
be figured out. In our team, members were not experts in their fields but few things were common and that are prerequisite for building any project i.e., Determination and Hard Working Mindset.
After facing several blockade, we continued to work for our goal and ended up in the finals. We were among the top 15 teams that were selected from all the 4 campuses of our college. We didn’t win the hackathon because we couldn’t figure out the Python and Flutter integration errors before the final evaluation but anyways the experience was worth remembering for all of us :)